The first IT (information technology), which is needed for work from home, is a mechanism for accessing the in -house network from home, that is, remote access.Here, we will explain typical means of remote access and security.
Work from home from remote access
To realize working from home, you need a communication infrastructure that can access the internal network from your home.A communication infrastructure that accesses the server at the workplace from home, browsing the data and materials necessary for the work, and using business applications and groupware, is indispensable.In order to achieve a work from home without stress, a communication line with a certain band (line speed) between the company and home is required.
Fortunately, Japan is one of the world's leading broadband powers in the world, with optical fiber and ADSL broadband lines to the level of metropolitan areas and prefectural governments in each prefecture, but also local small and medium -sized cities.There is.Internet access using the broadband line can be used for several thousand yen per month.In recent years, most of the remote access to work from home is the most commonly used broadband Internet.
By the way, about 10 years ago, there were no communication lines that could be used in an ISDN line with a bandwidth of 64 kbps or an analog phone line with a bandwidth of about 56 kbps.However, with today's broadband line, the bandwidth will be more than 10 times.Thanks to the development of telecommunications infrastructure over the past 10 years, stress associated with home, such as response and communication costs, has been significantly reduced.
Such a remote access method is broadly divided into classical dial -up connection and Internet VPN.
Classic dial -up connection
The dial -up connection refers to the form of calling the connection destination phone number (access point) when the user (worker) needs to connect and connects to an internal network via the ISDN or analog telephone line.。
For this reason, a server for incoming calls, called a dial -up server, is installed between the ISDN line net or analog telephone network and the internal network (Fig. 1).The dial -up server keeps waiting for a connection request from the user.The dial -up server used to use a dedicated hardware before, but has recently used routers with built -in ISDN port (BRI or PRI).Dedicated hardware can be connected from an analog telephone line, but if you use a router, you can only connect ISDN or PHS (PIAFS).
Figure 1 Remote access by dial -up connection
On the user (home worker), connect an ISDN card or modem to a PC and connect it using a PPP client software.If you use a PPP client that is standard on the OS such as Windows and Mac OS, you can use resources such as servers and printers on the internal network, just like PCs that are directly connected to the internal network after dialing.。
Inexpensive ISDN ports compatible routers, for example, remote access can be achieved simply by installing Yamaha's NVR500, so "I want to introduce a home -from -home work on a trial basis", "The number of users is small", "Data used in home work".It is suitable when the character information is mainly and the amount of data is small.
This is the Internet VPN
Internet VPN (Virtual Private Network) refers to the technology and mechanism that builds Virtual Private Network on the Internet.
To introduce an Internet VPN, a device called a VPN gateway shall be installed between the Internet and the internal network (Fig. 2).The Internet is a network (public network) that anyone can use freely, and there is a danger of eavesdropping and falsification of communication content.In order to perform secure communication on the Internet, communication is encrypted between the VPN gateway and the user PC with VPN client software.
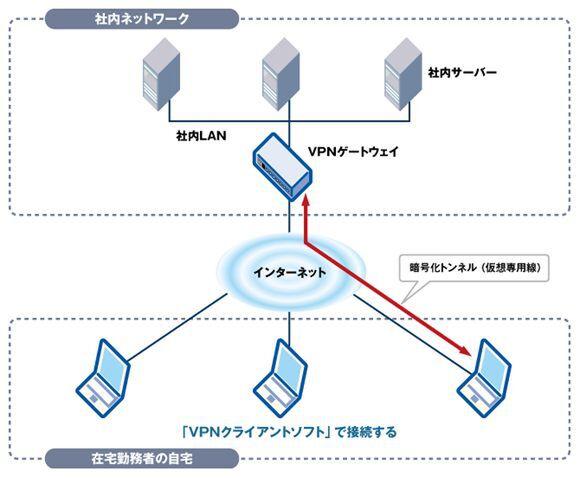
Figure 2 Remote access by Internet VPN (IPSEC, PPTP)
Table 1 is a comparison of typical technologies used in Internet VPNs.Of these, "IPSEC (Security Architecture for Internet Protocol)" is the oldest technology.As a result of many years of development, the functions are abundant, but the content is complicated and the introduction and settings are high.IPSEC's VPN gateway is often used by corporate routers such as Cisco Systems, and is rarely implemented in low -cost routers for consumers.
Table 1 Comparison of Internet VPN technology
In addition, IPSEC implementation has a "dialect" for each manufacturer, and client PCs generally introduce special client software provided by VPN gateway manufacturers.IPSEC is also a VPN protocol that is often used for corporate connections (LAN connection), but is not often used in remote access to work from home, which focuses on terminal connections.
Another PPTP (Point-to-Point Tunneling Protocol) is a VPN technology developed by Microsoft.Therefore, Windows is equipped with PPTP server (VPN gateway) and client functions as standard.Since Windows is the standard, there are few problems due to differences in implementation, and the Windows PPTP client function is used as it is, regardless of the router of any manufacturer.
While IPsec targets TCP/IP, PPTP also supports protocols other than TCP/IP (novels IPX/SPX, IBM NetBeui).The PPTP VPN gateway function is implemented in relatively inexpensive routers such as Yamaha NVR500, and the introduction threshold is lower than IPsec.Currently, PPTP is the mainstream of remote access to realize terminal connection.
SSL-VPN that can be used in web browsers
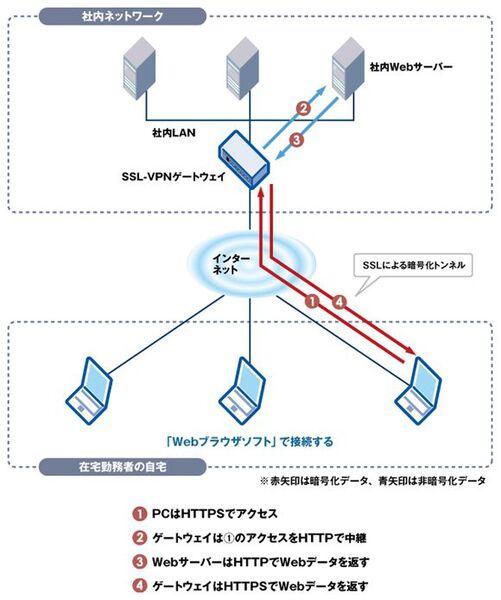
SSL-VPN is basically a technology that uses general web browsers such as Internet Explorer and Firefox to access internal networks.The hurdle to introduce is low because it can be used only with the SSL (Secure Sockets Layer) communication function equipped with a web browser.
The SSL-VPN also has a VPN gateway between the Internet and the internal network (Figure 3).This is especially called "SSL-VPN Gateway".SSL-VPN gateway is mostly hardware products such as Juniper Networks "SA (Secure Access)" and F5 Networks "Firepass", and the rest are software that runs on Linux and commercial UNIX OS.For corporate users, dedicated hardware products are the mainstream, but research and educational institutions use open source software.
Figure 3 Remote access by SSL-VPN
The core technology of SSL-VPN Gateway is "Reverse Proxy".This mechanism is explained using the arrow (direction of the data packet) in FIG.
As described above, the basics of SSL-VPN are using a web browser.However, SSL-VPN gateway vendors have SSL-VPN client software to meet the request of using SSL-VPN from a web browser.By using this, you can use SSL-VPN like IPsec and PPTP.
On the other hand, business applications, e -mails, groupware, etc. have been converted to web applications one after another, and on user PCs, web browsers have become sufficient.In other words, the arrival of the "All Over Web (All Over Http)" has led to the possibility that the mainstream of remote access will be SSL-VPN.
Mechanism to maintain security
Doing work using remote access is, in other words, taking out the company's confidential information out of the company and handling it.Therefore, it is necessary to pay much attention to prevent information leakage, which requires a mechanism to prevent eavesdropping and tampering on the communication route, and a mechanism to authenticate whether the communication partner is legitimate.
Eavesdropping on communication routes and prevention of tampering
First, let's consider eavesdropping and tampering on the communication route.If it is a dial -up connection, first of all, the responsibility of the carrier (NTT East, KDDI, SoftBank Telecom, etc.), which is the provider of ISDN and analog telephone lines, is ensured.If the safety is further enhanced, the following descriptions should be encrypted.
On the other hand, Internet VPN uses encryption to prevent eavesdropping and tampering.In IPsec, both the common key code and the public key code can be used.3des-CBC (key length 168 bits) and AES (key length 128-256 bits) are often used as encryption algorithms.
PPTP, which is commonly used in Windows, uses a common key code, and MPPE (Microsoft Point-to-Point Encryption) is used for the encryption algorithm.This MPPE is a cryptographic algorithm complies with the RC4 with a key length of 40-128 bits, and may not be able to maintain safety depending on the usage method, like RC4.L2TP, which has improved PPTP, does not support encryption, but is used in combination with IPsec to perform encryption.
SSL-VPN uses SSL in encrypted algorithm as described above.SSL uses a common key code for data encryption, but is a "hybrid code" that uses a public key code to replace the common key.
Certification of telecommunications partner
In remote access, whether the communication partner is a legitimate partner is first authenticated by the combination of ID and password (account information).When account information is abused, others who have become themselves can use remote access to steal the company's confidential information.However, it is difficult to completely prevent account plagiarism.Rather, it is necessary to have a mechanism that does not have to be a problem even if the password is broken, or a mechanism that does not require users to remember the password.
A mechanism that does not bother even if the password is broken is the method of "callback" in the dial -up connection.This means that immediately after authenticating with ID and password, the dial -up server is turned off and transmitted again from the dial -up server to the user.
At this time, the phone number of the home is registered in the dial -up server user database, so even if others illegally use the ID and password, the callback cannot be received.In addition, there is a "two -factor authentication" that authenticates users with two elements by using another element in addition to the password.Already, the digital certificate contained in the IC card USB token, and the user authentication using the biological authentication and one -time password described later are widely used.
Mechanisms that do not need to remember the password include biological authentication that uses personal information such as fingerprints, iris and veins, and one -time passwords.The initial one -time password requires a password generator (IC card, token, etc.), and the trouble of issuing the device or the case of loss was regarded as a problem, but recently there is no need for devices such as "matrix authentication".Technology is also practical.