In March of this year (2013), a large DDOS attack occurred, with two spamhaus Project, a spam countermeasure organization, and CloudFlare, which supported the organization.This time, there was a report on the countermeasures in the program "DNS Day" of "Internet Week 2013" held in Akihabara, Tokyo, so I will explain this DDOS attack method and its countermeasures here.
Large -scale DDOS attack of "peak trafficking 300Gbps super super"
"DDOS" is an abbreviation of Distributed Denial of Service, an attack method that uses overloading of many places (devices) to overload the server and network of the opponent, and drives it into a state of inoperable service.DDOS attacks have been performed many times before, but the size (traffic amount) is only several hundred Mbps to several tens of Gbps, and rarely exceeds 100 Gbps.
On the other hand, the DDOS attack is extremely large, exceeding 300 Gbps, which has a maximum of 300 Gbps, and has been confirmed to have impaired communication in some areas.In addition, the cause of the increase in the attack on the attack was that DNS was considered a major problem among Internet officials.
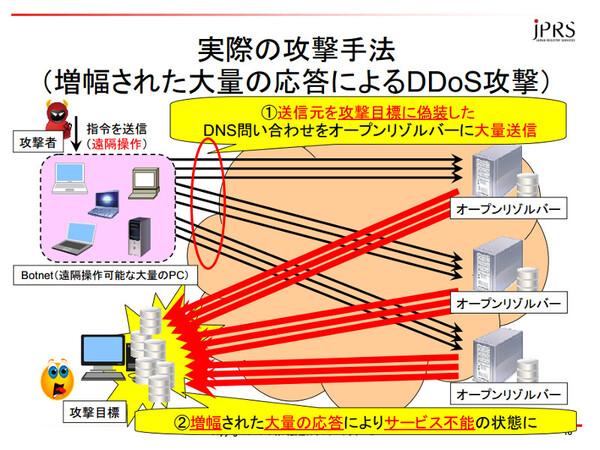
The attack is caused by sending a query that disguised the sender to the cache DNS server called "open resolver" to the attack target IP address.Open resolver, which receives a query that disguised the sender, will resolve the DNS name as the correct query, and return the result to the disguised IP address.
There are countless open resolvers that can be abused by attacks, and sending a disguised query will result in a large amount of DNS response to the attack target.The characteristics of DNS's "the response is larger (amplified)" and the existence of a large number of open resolver that can be abused by attacks have made a very large DDOS attack.This attack method is called "DNS amplifier attack" or "DNS reflector attack".
Conceptual diagram of this attack (quoted from JPRS Morishita's lecture materials at the IoT Study Group)
Initiatives to eradicate open resolver
By the way, what is an "open resolver" that has been abused by this attack and helped to enlarge the attack?
According to the DNS mechanism, it should be clear that individual cache DNS servers should provide services.For example, if it is an ISP, only customers who have a service contract should provide the function of the cash DNS server only for companies for companies.However, there are actually many cash DNS servers on the Internet that can actually accept queries from anywhere.This is called "open resolver".
大規模攻撃を助け、“有害さ”が無視できないものとなったオープンリゾルバーに対して、インターネット関係者はさまざまな対策を進めている。DNSサーバーが攻撃者の“送信元偽装”を見破る「送信元検証(イングレスフィルタリング)」※技術を導入するのが理想的だが、これは世界中のネットワークで適用しなければ大きな効果は望めず、対応が進んでいないのが現状である。※RFC 2827(BCP 38)で定義された仕組み。イングレス(ingress:進入)の文字通り、自ネットワークに入ってくる送信元を偽装したパケットに対するフィルタリングを行う。
Therefore, at the same time, measures on individual DNS servers are being taken."Eliminating the open resolver" is one of them, and the cache DNS server should define the subject to provide services and limit access from other networks.
However, in terms of theory, it is easy to say, "The out -of -the -art cache DNS server is hanging out of external users", and "once a customer, but after moving to other companies' services, it was related to DNS.In some cases, the settings have not been changed, and it seems that it is not easy to actually add access restrictions.It is difficult to contact people who are using outside or those who are no longer the company without noticing, and even if they are contacted, "the internet will not be used (it will)".The problem is that there are cases where complaints are included.
Of course, based on such things, we cannot leave a large open resolver.Even the major ISP, which could not easily eliminate the open resolver due to the history mentioned above, is gradually embarking on the eradication of open resolver.
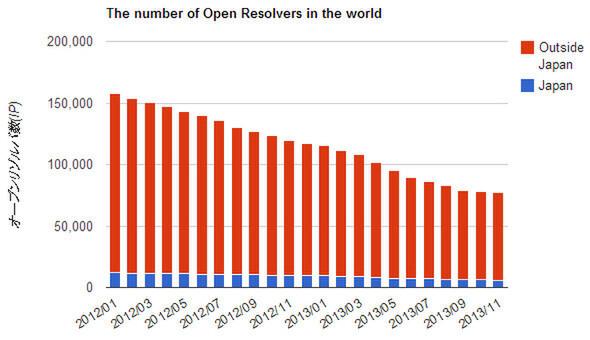
Changes in the number of open resolver numbers in the world (left) and Japan (quoted from JPCERT/CC's "Open Resolver Confirmation Site")
JPCERT/CC has released the "Open Resolver Confirmation Site", is it not set to use the open resolver on the user's PC, or is the Internet connected device (broadband router, etc.) an open resolver?I'm calling for confirmation.It would be better to check again and review the settings on this occasion.
▼ Open Resolver Confirmation Site (JPCERT/CC) ▼ Overview of DNS reflector attacks using open resolver -You are also perpetrators (JPRS Morishita's lecture material: PDF) ▼ Open Resolver (Open Resolver (Open Resolver)) Caution for) (JPNIC)
Authority DNS server and JP DNS countermeasures
What I have seen so far is a countermeasure on the cash DNS server.However, in the DNS amplifier attack (DNS reflector attack), not only the cash DNS server but also the authority DNS server can be used.Therefore, the authority DNS server requires measures, but the major problem here is that the authority DNS server cannot limit to a specific access source (it is necessary to accept queries from anywhere on the Internet).。
Therefore, a technology called "DNS RRL (Response Rate Limiting)" that can be applied to authority DNS servers has been developed.To explain the mechanism roughly, it is "limit the number and size of the high -frequency DNS response that can be regarded as the same."Although it does not completely prevent DNS amplifier attacks, it is possible to reduce the effect as a stepping stone and reduce the scale of the attack.In Japan, the Japanese registry service (JPRS), which manages and operates JP domain names, is introducing.It can be said that measures for authority DNS servers are steadily progressing.
What you want to ask the network manager
In order to operate the Internet stably, DNS stable operation is important.If DNS cannot provide the service correctly, you will not be able to connect to the other party correctly or send an email correctly.
On the other hand, DNS is a distributed database, and the cooperation of a wide range of network administrators, including companies and universities, is indispensable for the cooperation of not only services such as ISPs and hosting operators.This is because DNS clients operated by the user side, cash DNS server in charge of name resolution, and authority DNS server that manages information on each domain name can be realized by facilitating DNS stable operation.。
When managing and operating the DNS server, three points are now: "Separation of cash DNS server and authority DNS server", "restrictions on service provision in the cash DNS server", and "stopping cash DNS server functions in authority DNS servers".It can be said that it is an essential matter.If it is necessary to manage large data that can be used for attacks such as SPF, DKIM, and DNSSEC, please consider the introduction of DNS RRL to the authority DNS server.In the article of "JPRS Topics & Column" released by JPRS, the importance of these measures is summarized in an easy -to -understand manner.
▼ Is the DNS safe and stability of DNS -Is it okay for your DNS server?~ (JPRS, PDF)
The Internet is indispensable for our daily life.For the stability, I would like to ask for a wide range of cooperation of network administrators.